суббота, 31 марта 2012 г.
среда, 28 марта 2012 г.
вторник, 27 марта 2012 г.
воскресенье, 25 марта 2012 г.
суббота, 24 марта 2012 г.
пятница, 23 марта 2012 г.
четверг, 22 марта 2012 г.
Beyond "When developer’s api simplify user mode rootkits developing… "
- A half month ago I posted a link to the article published in Hakin9 Mobile. Article "When developer’s api simplify user mode rootkits developing…" refers to several published articles in Hakin9 and Hakin9 Extra in turn as aggregation of ideas when group policies are easy to bypass. Also, it's first part of article should be published after InfoSecurity Russia 2011 Conference where I was a Hakin9 Representative. So, I provide links to all my previous article to extend example understanding were highlight in this article. By the way, to get relevant information outside my blog (this or another) you may follow a SlideShare Channel.
- Share
- ShareA Security System That Changed The World from Network Security Hakin9 02 2011
- ShareIs Data Secure On The Password Protected Blackberry Device from Network Security Hakin9 02 2011 3
- ShareThe Backroom Message That’s Stolen Your Deal from Mobile Security Hakin9 04 2011
- ShareWhy is password protection a fallacy a point of view
- ShareDoes your black berry smartphone have ears
- ShareTo get round to the heart of fortress
- ShareWhen developer's api simplify user mode rootkits developing
среда, 21 марта 2012 г.
вторник, 20 марта 2012 г.
понедельник, 19 марта 2012 г.
воскресенье, 18 марта 2012 г.
суббота, 17 марта 2012 г.
пятница, 16 марта 2012 г.
Without The Right Message, Twitter Is No Better For Your Brand Than A Fax Machine
- ShareWithout The Right Message, Twitter Is No Better For Your Brand Than A Fax Machine | Fast Company
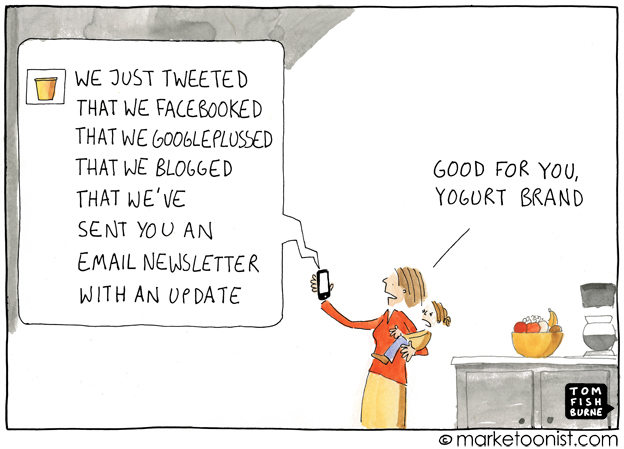 BY Expert Blogger David Brier | 03-14-2012 | 1:48 PM This blog is written by a member of our expert blogging community and expresses that...
BY Expert Blogger David Brier | 03-14-2012 | 1:48 PM This blog is written by a member of our expert blogging community and expresses that...
Proof-of-concept RDP
- ShareProof-of-concept RDP vulnerability code already available. Patch Windows now | Naked Security
 Graham Cluley is senior technology consultant at Sophos. The readers of Computer Weekly voted him security blogger of the year in 2009 an...
Graham Cluley is senior technology consultant at Sophos. The readers of Computer Weekly voted him security blogger of the year in 2009 an...
четверг, 15 марта 2012 г.
среда, 14 марта 2012 г.
вторник, 13 марта 2012 г.
When developer’s api simplify user mode rootkits developing…
This is a series of articles about shell extensions that enhance high-level features of any operation system. However, such possibilities not only enrich platform but simplify developing trojans, exploits that leads to the new security holes. Mostly this kind of extensions are known as usermode rootkits.
Read more in Hakin9 Magazine or my SlideShare channel
Ярлыки:
API,
BlackBerry API,
Developer API,
Developer's API,
Developers API,
Hakin9,
When developer’s api simplify user mode rootkits developing,
Yury Chemerkin
FBI says $700K charged in Anonymous' Stratfor attack
During the court case for Jeremy Hammond--the Antisec hacker busted for stealing data in the Stratfor breach--the FBI says charges made with stolen credit card information equals $700,000. Read this blog post by Dara Kerr on Security.
Read more
Read more
понедельник, 12 марта 2012 г.
Hash visualizing of typed passwords
Both services are examine the more secure stage between clear and masked passwords by visualizing a hashed password's representation with colors and/or histogram to find out whether right or wrong your entered password.
JavaScript RGB Password
HashMask
Result with the word "SupErP@$$w0rD"
JavaScript RGB Password
HashMask
Result with the word "SupErP@$$w0rD"
воскресенье, 11 марта 2012 г.
Official BlackBerry PlayBook Mini Keyboard is coming with 128bit encryption?
While there's an array of unofficial third-party keyboards willing to pair up with your 7-inch RIM slate, an approved peripheral is likely to be the better option. Read More
суббота, 10 марта 2012 г.
пятница, 9 марта 2012 г.
Dome9 Security Launches Free Cloud Security

Dome9 Security Launches Free Cloud Security For Unlimited Number Of ServersDark ReadingMarch 7, 2012 – Dome9 Security™, the leading provider of cloud security firewall management for public and private clouds, as well as for dedicated and virtual...
Via www.darkreading.com
Google+ To RSS: Create An RSS Feed From Your Google Plus Stream
Both Facebook and Twitter provide ways to fetch your stream of updates via RSS into an RSS feed reader. Google+ on the other hand doesn’t have any such option. Google+ to RSS is a third-party tool that aims to fill this hole. It lets you create an RSS feed of public Google+ updates and requires your Google+ profile ID, API key and an email address. Private or limited status updates will not show up in the feed though.
Read more
Read more
Llama: Transform Your Android Phone to A Fully Automated Bot
Having different profiles for your Android device is super handy. You can set up different volumes and notifications for different environments such as work and home. While it is cool to be able to manually switch your Android profiles when you need to, automatic Android profile switching is even better.
Llama is a great location aware profile switcher. What that means to you is, you can set up Llama to automatically change your profile according to the locations/events/conditions. For example, you can get it to silent your phone when you get to the movie theater or change to a more business-like set of alerts when you arrive at work. Best of all, it doesn’t suck up your battery life.
Read more
Llama is a great location aware profile switcher. What that means to you is, you can set up Llama to automatically change your profile according to the locations/events/conditions. For example, you can get it to silent your phone when you get to the movie theater or change to a more business-like set of alerts when you arrive at work. Best of all, it doesn’t suck up your battery life.
Read more
Android Tracking – from a forensic point of view
In article on iPhoneTracking, Apple’s crowd-sourced location based service was explain. Obviously Android has to do something similar to provide a good user experience using location based services. Read more..
iPhone Tracking – from a forensic point of view
Apple, on the other hand, stated that: “in no way Apple does tracking movements of iPhone users”. What Apple admits is to provide a well designed CoreLocation Framework. Read more...
Pwn2Own 2012: Google Chrome first to fall
At last year’s CanSecWest Pwn2Own hacker contest, Google Chrome was the only browser left standing. This year, Chrome was the first to fall, thanks to an impressive exploit from a team of French hackers. Read more...
BlackBerry Device Service for BlackBerry Mobile Fusion
The biggest area of interest is around the specific details of the BlackBerry® Device Service component of BlackBerry Mobile Fusion. Simply put, the BlackBerry Device Service is to BlackBerry® PlayBook™ tablets as the BlackBerry® Enterprise Server is to BlackBerry smartphones. The BlackBerry Enterprise Server manages your current BlackBerry smartphones, and the BlackBerry Device Service allows you to manage and secure your organization’s BlackBerry PlayBook tablets – and, moving forward, it will also manage BlackBerry® 10 smartphones. But that’s not all that BlackBerry Device Service offers – there’s even more going on underneath the covers. More...
среда, 7 марта 2012 г.
Interview with Hakin9
In February I gave Hakin9 an interview. Hakin9 is known as online, payable weekly magazine totally devoted to IT security. It covers techniques of breaking into computer systems, defense and protection methods, tools and latest trends in IT Security. Hakin9 is published by Software Press Sp.z.o.o (Software Wydawnictwo) that is a Poland-based company with many years experience in publishing magazines.
My interview was published in Hakin9 Magazine (main issue) on March 1st and it's available to read on Hakin9 web-site Hakin9 3/2012: DNS Cache Poisoning issue as well as on my SlideShare channel by clicking Interview with Yury Chemerkin or by clicking Publication's Portfolio.
My interview was published in Hakin9 Magazine (main issue) on March 1st and it's available to read on Hakin9 web-site Hakin9 3/2012: DNS Cache Poisoning issue as well as on my SlideShare channel by clicking Interview with Yury Chemerkin or by clicking Publication's Portfolio.
суббота, 3 марта 2012 г.
About Yury Chemerkin
This is a brief summary about me, my biography, interests and contacts.
Well, I graduated at Russian State University for the Humanities in 2010. I defended my diploma thesis on the BlackBerry infrastructure's vulnerability. At present postgraduate at RSUH and now I’m researching BlackBerry and Cloud Security. I'm an Information Security Researcher since 2009 and I’m experienced in Reverse Engineering, Programming, Cyber & Mobile Security Researching, Documentation, Cloud Security, Security Writing.
I have scientific and applied interests in the sphere of forensics, cyber security, AR, AI, perceptive reality, semantic networks, mobile security and cloud computing. I'm researching Cloud Infrastructure and the effects of the trust bot-net & forensic techniques on the human privacy.
I have published works in HAKIN9 - IT Security Magazine as well as SlideShare channel where you can find them. Also, they might find traces of mine on the most popular social networks or instant messengers. Contact details:
Each my blog usually stores a page “Contacts” where everyone can find all of my social contacts. Re.Vu and Windows Live covers almost social contacts while my emails and IMs are below:
| Emails :: | |
| Google Email :: | yury.chemerkin@gmail.com |
| Yahoo Email :: | yury.chemerkin@yahoo.com |
| AIM (AOL) Email :: | yurychemerkin@aim.com |
| Live Email :: | yury.chemerkin@hotmail.com |
| IMs :: | |
| Windows Live :: | Yury Chemerkin (yury.chemerkin) |
| GTalk :: | Yury Chemerkin (yury.chemerkin) |
| Y!Messenger :: | Yury Chemerkin (yury.chemerkin) |
| AIM :: | Yury Chemerkin (yurychemerkin) |
| Skype :: | Yury Chemerkin (yury.chemerkin) |
You also can scan qr-code to get my Re.Vu data faster.

By the way, my blogs or some kind of them are list below:
| Viadeo Group | http://goo.gl/HE1H1 |
| Facebook Pages | http://goo.gl/4MgaW |
| LinkedIn Group | http://goo.gl/fCah4 |
| Scoop.it | http://www.scoop.it/u/yury-chemerkin |
| Tumblr | http://www.tumblr.com/blog/yurychemerkin |
| Blogger | http://security-through-obscurity.blogspot.com/ |
| Wordpress | http://yurychemerkin.wordpress.com/ |
Подписаться на:
Комментарии (Atom)


